Set load balancer rules
Load balancer rules determine how traffic is routed to your virtual machines based on conditions such as protocols, ports, and paths.
This guide explains how to configure and manage load balancer rules to optimise traffic distribution accross your infrastructure.
Common use cases for load balancer rules include:
- Web traffic distribution: Route incoming HTTP/HTTPS requests (ports 80/443) across multiple web servers
- Database load balancing: Distribute database connections (for example MySQL on port 3306) across database replicas
- Application-specific routing: Direct specific application traffic (for example game server traffic on custom ports) to appropriate backend servers
- Protocol-based rules: Set up rules to handle different protocols like TCP or UDP depending on your application needs
For example:
- A web application might use a rule to forward all HTTP traffic on port 80 to multiple web servers
- A microservices architecture could use different rules to route requests to specific services based on paths or ports
- Gaming applications might use UDP-based rules to handle real-time game traffic
- Improve application availability
- Scale your infrastructure
- Optimize resource utilization
Add a load balancer rule
Clicking the Add another rule button, or the Edit button for an existing rule will take you to the load balancer rule form.
Protocol and ports
When setting up a load balancer rule, you'll first need to specify how traffic should flow through your load balancer. This involves choosing which protocol to use and defining both the incoming and destination ports.
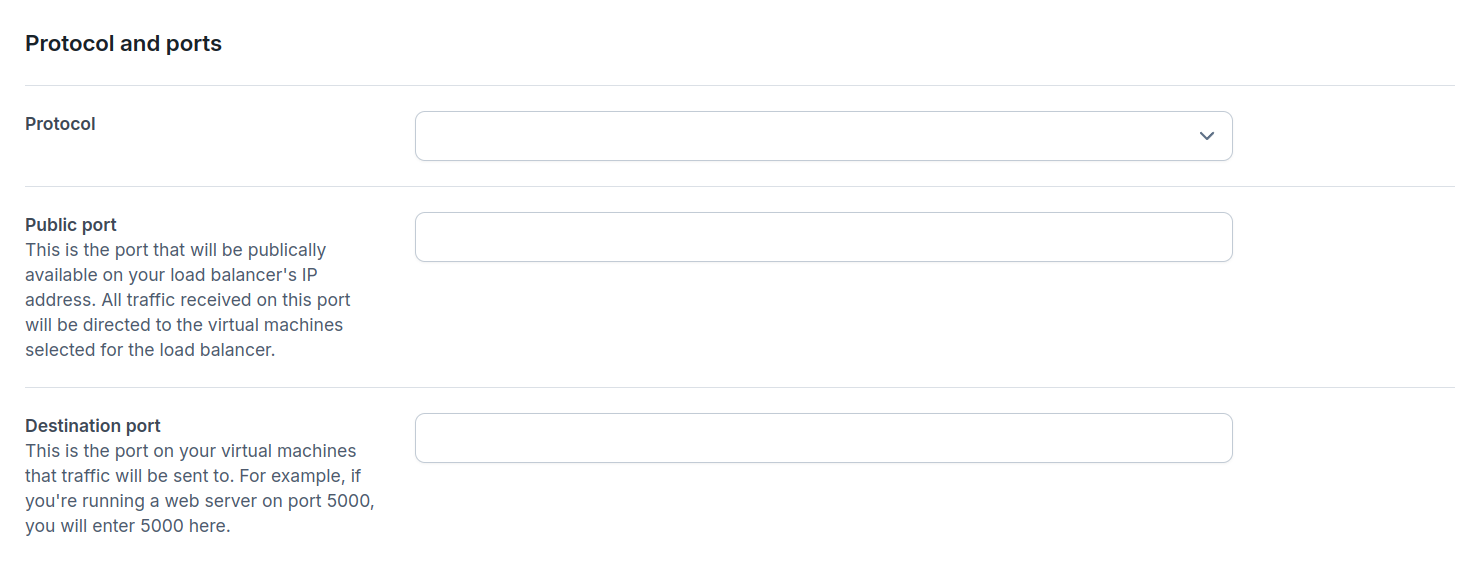
- Protocol - This is the protocol the rule will apply to, choose between
HTTP,HTTPS, andTCP. A single load balancer can work on multiple protocols by creating multiple rules. - Public port - This is the port that will be publicly available on your load balancer's IP address. All traffic for the selected protocol received on this port will be handled by this rule.
- Destination port - This is the port on your virtual machines that traffic will be sent to. For example, if you're running a web server on port 5000, you will enter 5000 here.
Configure a Healthcheck
Enable Healthcheck to monitor your virtual machines' health. When enabled, you'll need to configure options to allow the load balancer to correctly assess the health of your backend services.
If a virtual machine fails consecutive health checks, the load balancer will automatically stop routing traffic to that instance until it recovers, helping to prevent requests from being sent to malfunctioning servers.
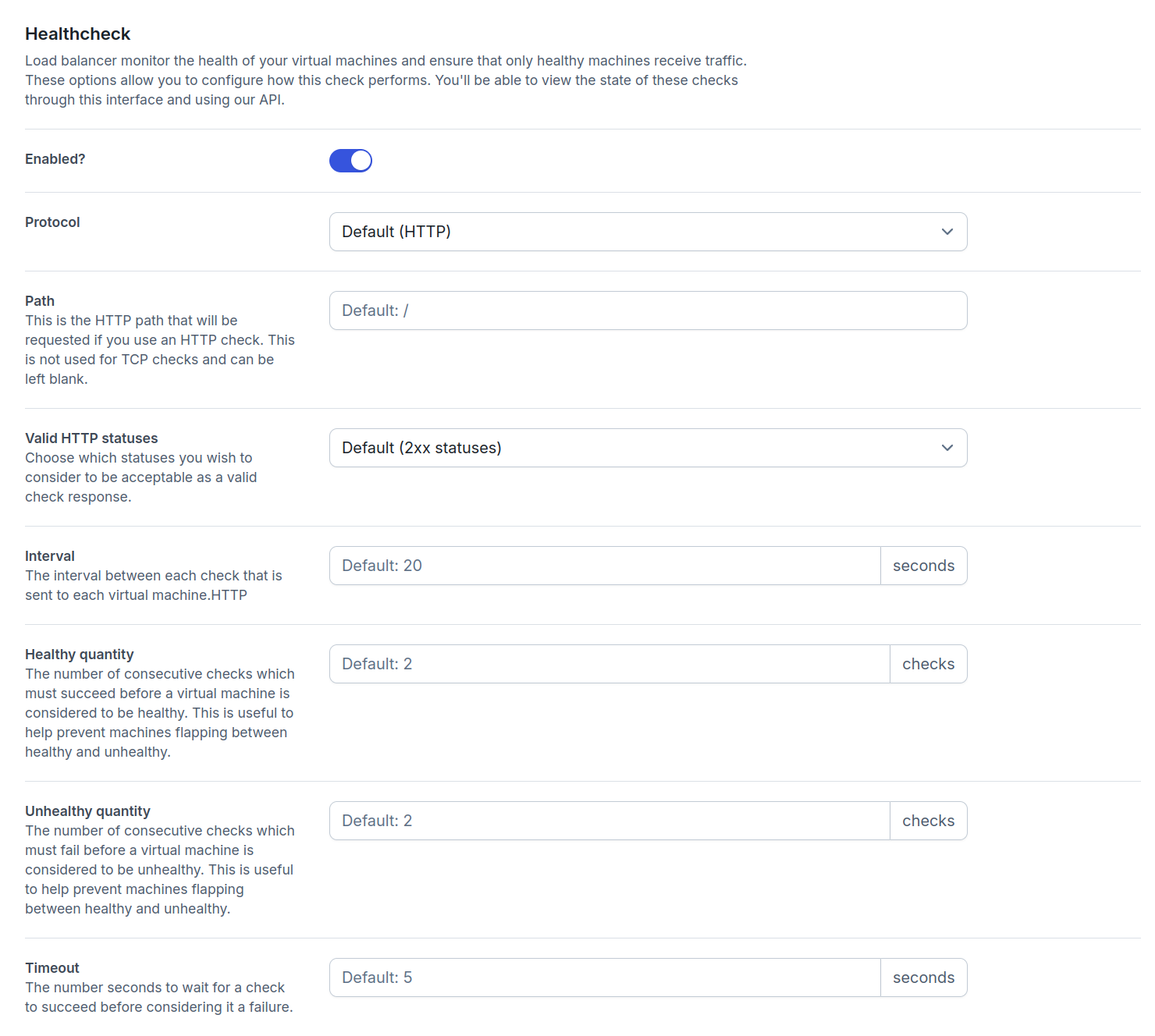
- Protocol - Choose between
HTTPorTCPfor health checks. - Path - (HTTP only) The endpoint path to check (for example
/healthor/status). - Valid HTTP status - (HTTP only) The HTTP status code(s) that indicate a healthy response.
- Check interval - How frequently the health check should be performed.
- Healthy threshold - Number of consecutive successful checks required to mark a virtual machine as healthy.
- Unhealthy threshold - Number of consecutive failed checks before a virtual machine is marked as unhealthy.
- Timeout - Maximum time to wait for a health check response before considering it failed.
Advanced options
The advanced options for a load balancer rule allow you to fine-tune how traffic is distributed and handled between your load balancer and virtual machines. These options include the load balancing algorithm, encryption of backend traffic, and the use of the proxy protocol.
- Algorithm - This dictates how a virtual machine is chosen by the load balancer:
- Round robin (default) - Distributes traffic to virtual machines in a rotation.
- Least connections - Sends traffic to the virtual machine with the fewest connections currently open.
- Sticky - Identifies requests coming from the same client and always sends those requests to the same virtual machine.
- Encrypt backend traffic - If enabled, the connections between the load balancer and virtual machines will be encrypted using the load balancer's backend certificate (which can be downloaded from the load balancer's overview page). Otherwise, this traffic will be unencrypted.
- Use proxy protocol - If enabled, the Proxy Protocol will be used to ensure the client's IP address is preserved as traffic is proxied through the load balancer to your virtual machines.